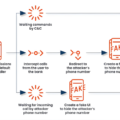
Hacking ChatGPT by Planting False Memories into Its Data
This vulnerability hacks a feature that allows ChatGPT to have long-term memory, where it uses information from past conversations to…
5 Actionable Steps to Prevent GenAI Data Leaks Without Fully Blocking AI Usage
Since its emergence, Generative AI has revolutionized enterprise productivity. GenAI tools enable faster and more effective software development, financial analysis,…
Free Sniper Dz Phishing Tools Fuel 140,000+ Cyber Attacks Targeting User Credentials
More than 140,000 phishing websites have been found linked to a phishing-as-a-service (PhaaS) platform named Sniper Dz over the past…
UAE, Saudi Arabia Become Plum Cyberattack Targets
Hacktivism-related DDoS attacks have risen 70% in the region, most often targeting the public sector, while stolen data and access…
New Cryptojacking Attack Targets Docker API to Create Malicious Swarm Botnet
Cybersecurity researchers have uncovered a new cryptojacking campaign targeting the Docker Engine API with the goal of co-opting the instances…
U.K. Hacker Charged in $3.75 Million Insider Trading Scheme Using Hacked Executive Emails
The U.S. Department of Justice (DoJ) has charged a 39-year-old U.K. national for perpetrating a hack-to-trade fraud scheme that netted…
FERC Outlines Supply Chain Security Rules for Power Plants
The US Federal Energy Regulatory Commission spelled out what electric utilities should do to protect their software supply chains, as…
Crooked Cops, Stolen Laptops & the Ghost of UGNazi
A California man accused of failing to pay taxes on tens of millions of dollars allegedly earned from cybercrime also…