Quantum Leap: Advanced Computing Is a Vulnerable Cyber Target
At Black Hat USA, researchers from Bitdefender and Transilvania Quantum will showcase how attackers can target quantum-based infrastructure. At Black…
Russian Hacktivists Sanctioned for US Critical Infrastructure Attacks
“CARR” hackers have managed to gain control over ICS and SCADA systems in the US and Europe. “CARR” hackers have…
Kaspersky Is an Unacceptable Risk Threatening the Nation’s Cyber Defense
As geopolitical tensions rise, foreign software presents a grave supply chain risk and an ideal attack vector for nation-state adversaries.…
Experts Uncover Chinese Cybercrime Network Behind Gambling and Human Trafficking
The relationship between various TDSs and DNS associated with Vigorish Viper and the final landing experience for the user A…
PINEAPPLE and FLUXROOT Hacker Groups Abuse Google Cloud for Credential Phishing
A Latin America (LATAM)-based financially motivated actor codenamed FLUXROOT has been observed leveraging Google Cloud serverless projects to orchestrate credential…
Chinese Forced-Labor Ring Sponsors Football Clubs, Hides Behind Stealth Tech
An illegal gambling empire fueled by modern-day slavery is being propped up by high-profile sponsorships — and defended with sophisticated…
MSPs & MSSPs: How to Increase Engagement with Your Cybersecurity Clients Through vCISO Reporting
As a vCISO, you are responsible for your client’s cybersecurity strategy and risk governance. This incorporates multiple disciplines, from research…
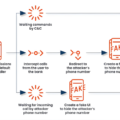
How to Set up an Automated SMS Analysis Service with AI in Tines
The opportunities to use AI in workflow automation are many and varied, but one of the simplest ways to use…