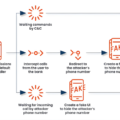
Goodbye? Attackers Can Bypass ‘Windows Hello’ Strong Authentication
Accenture researcher undercut WHfB’s default authentication using open source Evilginx adversary-in-the-middle (AitM) reverse-proxy attack framework. Accenture researcher undercut WHfB’s default…
China’s ‘Evasive Panda’ APT Spies on Taiwan Targets Across Platforms
The cohort’s variety of individual tools covers just about any operating system it could possibly wish to attack. The cohort’s…
Phish-Friendly Domain Registry “.top” Put on Notice
The Chinese company in charge of handing out domain names ending in “.top” has been given until mid-August 2024 to…
Sprawling CrowdStrike Incident Mitigation Showcases Resilience Gaps
A painful recovery from arguably one of the worst IT outages ever continues, and the focus is shifting to what…
Attackers Exploit ‘EvilVideo’ Telegram Zero-Day to Hide Malware
An exploit sold on an underground forum requires user action to download an unspecified malicious payload. An exploit sold on…
Chinese Hackers Target Taiwan and US NGO with MgBot Malware
Organizations in Taiwan and a U.S. non-governmental organization (NGO) based in China have been targeted by a Beijing-affiliated state-sponsored hacking…
Shocked, Devastated, Stuck: Cybersecurity Pros Open Up About Their Layoffs
Here’s a dose of reality from those on the frontlines and how they’re coping. Here’s a dose of reality from…
Wanted: A SBOM Standard to Rule Them All
A unified standard is essential for realizing the full potential of SBOMs in enhancing software supply chain security. A unified…