Telegram App Flaw Exploited to Spread Malware Hidden in Videos
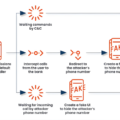
A zero-day security flaw in Telegram’s mobile app for Android called EvilVideo made it possible for attackers to malicious files…
How a Trust Center Solves Your Security Questionnaire Problem
Security questionnaires aren’t just an inconvenience — they’re a recurring problem for security and sales teams. They bleed time from…
Patchwork Hackers Target Bhutan with Advanced Brute Ratel C4 Tool
The threat actor known as Patchwork has been linked to a cyber attack targeting entities with ties to Bhutan to…
How to Reduce SaaS Spend and Risk Without Impacting Productivity
There is one simple driver behind the modern explosion in SaaS adoption: productivity. We have reached an era where purpose-built…
CrowdStrike Explains Friday Incident Crashing Millions of Windows Devices
Cybersecurity firm CrowdStrike on Wednesday blamed an issue in its validation system for causing millions of Windows devices to crash…
CISA Adds Twilio Authy and IE Flaws to Exploited Vulnerabilities List
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws to its Known Exploited Vulnerabilities (KEV) catalog,…
Microsoft Defender Flaw Exploited to Deliver ACR, Lumma, and Meduza Stealers
A now-patched security flaw in the Microsoft Defender SmartScreen has been exploited as part of a new campaign designed to…
Russia Adjusts Cyber Strategy for the Long Haul in War With Ukraine
Russia has cast aside its focus on civilian infrastructures and is instead targeting Ukraine’s military operations in myriad ways. Russia…