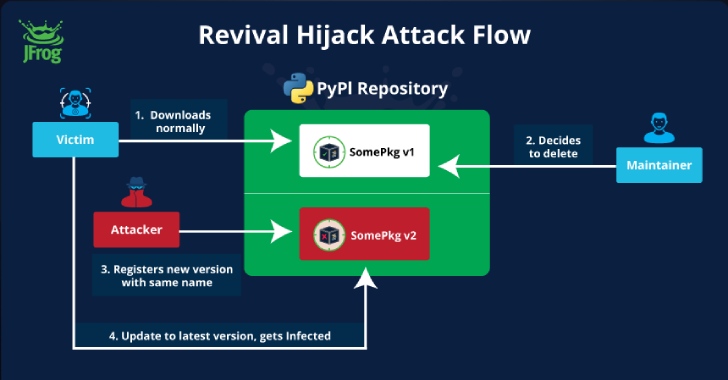
A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited in the wild in an attempt to infiltrate downstream organizations.
It has been codenamed Revival Hijack by software supply chain security firm JFrog, which said the attack method could be used to hijack 22,000 existing PyPI packages and result in “hundreds of thousands” of malicious package
A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited in the wild in an attempt to infiltrate downstream organizations.
It has been codenamed Revival Hijack by software supply chain security firm JFrog, which said the attack method could be used to hijack 22,000 existing PyPI packages and result in “hundreds of thousands” of malicious package