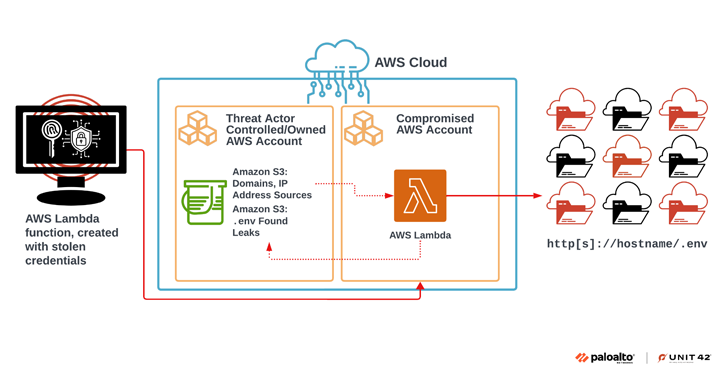
A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files (.env) that contain credentials associated with cloud and social media applications.
“Multiple security missteps were present in the course of this campaign, including the following: Exposing environment variables, using long-lived credentials, and absence
A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files (.env) that contain credentials associated with cloud and social media applications.
“Multiple security missteps were present in the course of this campaign, including the following: Exposing environment variables, using long-lived credentials, and absence